Difference between revisions of "Third-party software integration: Apache"
m (→SSL in Red Hat / CentOS) |
(→Red Hat / CentOS) |
||
| (41 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
{{TOCright}} __TOC__ | {{TOCright}} __TOC__ | ||
| − | Expose OpenKM directly from JBoss can be dangerous if you need the application to be accessed from Internet. Also this 8080 may be closed by a firewall. For these reasons, is a good idea expose your OpenKM installation through the standard web port 80. In the following steps we explain how to configure Apache to handle these request and forward to | + | Expose OpenKM directly from Tomcat or JBoss can be dangerous if you need the application to be accessed from Internet (for example https://issues.jboss.org/browse/JBAS-3861). As result you can be infected by [http://www.sophos.com/en-us/threat-center/threat-analyses/viruses-and-spyware/Mal~PerlBot-A.aspx PerlBot]. Also this 8080 may be closed by a firewall. For these reasons, is a good idea expose your OpenKM installation through the standard web port 80. In the following steps we explain how to configure Apache to handle these request and forward to Tomcat application server using the AJP13 protocol. |
From the Apache documentation: The AJP13 protocol is packet-oriented. A binary format was presumably chosen over the more readable plain text for reasons of performance. The web server communicates with the servlet container over TCP connections. To cut down on the expensive process of socket creation, the web server will attempt to maintain persistent TCP connections to the servlet container, and to reuse a connection for multiple request/response cycles. | From the Apache documentation: The AJP13 protocol is packet-oriented. A binary format was presumably chosen over the more readable plain text for reasons of performance. The web server communicates with the servlet container over TCP connections. To cut down on the expensive process of socket creation, the web server will attempt to maintain persistent TCP connections to the servlet container, and to reuse a connection for multiple request/response cycles. | ||
| + | |||
| + | {{Advice|You can see how to configure Apache with SSL at [[Third-party_software_integration:_Apache_SSL_and_more|Apache SSL and more]] article.}} | ||
| + | |||
| + | == Internal IP vs external IP == | ||
| + | Your OpenKM can be accessed from two different zones: Internet and LAN. This means that to access this server you need to use two IPs: external IP (Internet) and internal IP (LAN). | ||
| + | |||
| + | The internal IP address (also known as "local IP address") is the address that is assigned by your local network router that often begins with 192.168.x.x. These IP addresses can only be seen by other computers in your local network (LAN) and not by any computers connected in an external network such the Internet. | ||
| + | |||
| + | To reach the Internet or a computer in another network your computer is often assigned an external IP address, which can then be used to refer to the computer in your local network. | ||
| + | |||
| + | [[File:Internal ip.png|center]] | ||
| + | |||
| + | In the above picture, there are three computers in the local network that have each been assigned their own internal IP address by the router. The ISP is connected to the router and gives the router an external IP address that allows it to communicate with the Internet. On the Internet everyone sees your external IP address, but any information coming from the router is "converted" from the external IP address to the internal IP address. | ||
| + | |||
| + | So if you want your OpenKM installation accessible from both LAN and Internet, the trick here is configure the client computers to resolve your '''internal IP''' (192.168.0.50) if they are inside the LAN or the '''external IP''' if they are on Internet. To resolve the Internet IP (67.166.214.148) your computer uses the public DNS. So, you need to configure a sort of DNS server inside the LAN or modify every client [http://en.wikipedia.org/wiki/Hosts_%28file%29 host file] to resolve to the internal IP. | ||
== Debian / Ubuntu == | == Debian / Ubuntu == | ||
| Line 28: | Line 43: | ||
RedirectMatch ^/$ /OpenKM | RedirectMatch ^/$ /OpenKM | ||
<Location /OpenKM> | <Location /OpenKM> | ||
| − | ProxyPass ajp://127.0.0.1:8009/OpenKM | + | #ProxyRequests Off |
| + | #ProxyPreserveHost On | ||
| + | ProxyPass ajp://127.0.0.1:8009/OpenKM keepalive=On | ||
ProxyPassReverse http://openkm.your-domain.com/OpenKM | ProxyPassReverse http://openkm.your-domain.com/OpenKM | ||
</Location> | </Location> | ||
| − | ErrorLog /var/log/apache2/ | + | ErrorLog /var/log/apache2/openkm-error.log |
| − | CustomLog /var/log/apache2/ | + | CustomLog /var/log/apache2/openkm-access.log combined |
</VirtualHost> | </VirtualHost> | ||
</source> | </source> | ||
| + | |||
| + | {{Note|See all '''ProxyPass''' parameter at [http://httpd.apache.org/docs/2.2/mod/mod_proxy.html Apache Module mod_proxy documentation].}} | ||
The VirtualHost ServerName must be other than ServerName in the main Apache configuration. Enable this site configuration: | The VirtualHost ServerName must be other than ServerName in the main Apache configuration. Enable this site configuration: | ||
| Line 43: | Line 62: | ||
[warn] NameVirtualHost *:80 has no VirtualHosts | [warn] NameVirtualHost *:80 has no VirtualHosts | ||
you have to change the virtual host definition from <VirtualHost *> to <VirtualHost *:80>}} | you have to change the virtual host definition from <VirtualHost *> to <VirtualHost *:80>}} | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
{{Note|If you see an error like: | {{Note|If you see an error like: | ||
| Line 103: | Line 102: | ||
Now you can access your OpenKM installation from http://openkm.your-domain.com/. Another advantage of using Apache is that you can log OpenKM access and generate web statistics. | Now you can access your OpenKM installation from http://openkm.your-domain.com/. Another advantage of using Apache is that you can log OpenKM access and generate web statistics. | ||
| − | + | The syntax is as follows to run syntax tests for configuration files only: | |
| − | + | ||
| − | + | /usr/sbin/apache2 -t | |
| − | $ sudo | + | |
| + | == Red Hat / CentOS == | ||
| + | Here you can use the yum application manager to install Apache: | ||
| + | |||
| + | $ sudo yum install httpd | ||
| − | + | Remember to enable it at boot: | |
| − | + | $ sudo chkconfig httpd --level 2345 on | |
| + | |||
| + | Now create the file /etc/httpd/conf.d/openkm.conf with this content: | ||
<source lang="apache"> | <source lang="apache"> | ||
| − | <VirtualHost *: | + | <VirtualHost *:80> |
ServerName openkm.your-domain.com | ServerName openkm.your-domain.com | ||
RedirectMatch ^/$ /OpenKM | RedirectMatch ^/$ /OpenKM | ||
<Location /OpenKM> | <Location /OpenKM> | ||
| − | ProxyPass ajp://127.0.0.1:8009/OpenKM | + | ProxyPass ajp://127.0.0.1:8009/OpenKM keepalive=On |
ProxyPassReverse http://openkm.your-domain.com/OpenKM | ProxyPassReverse http://openkm.your-domain.com/OpenKM | ||
</Location> | </Location> | ||
| − | ErrorLog /var/log/ | + | ErrorLog /var/log/httpd/openkm-error.log |
| − | CustomLog /var/log/ | + | CustomLog /var/log/httpd/openkm-access.log combined |
| − | |||
| − | |||
| − | |||
</VirtualHost> | </VirtualHost> | ||
</source> | </source> | ||
| − | + | After that, restart Apache to make effective this configuration. | |
| − | |||
| − | $ sudo | + | $ sudo /etc/init.d/httpd restart |
| − | + | == Mac OS X == | |
| + | Edit the file called /etc/apache2/apache2.conf and configure a ServerName, enable proxy modules and mod_proxy: | ||
| − | + | <source lang="apache"> | |
| + | ServerRoot "/usr" | ||
| + | ServerName "your-domain.com" | ||
| − | + | LoadModule proxy_module libexec/apache2/mod_proxy.so | |
| + | LoadModule proxy_ajp_module libexec/apache2/mod_proxy_ajp.so | ||
| − | + | <IfModule mod_proxy.c> | |
| + | ProxyRequests Off | ||
| + | <Proxy "*"> | ||
| + | AddDefaultCharset off | ||
| + | Allow from all | ||
| + | Deny from all | ||
| + | Order Deny,Allow | ||
| + | </Proxy> | ||
| + | ProxyVia On | ||
| + | </IfModule> | ||
| + | </source> | ||
| − | + | Now create the configuration file /etc/apache2/sites/openkm.conf with this content: | |
| − | + | <source lang="apache"> | |
| − | + | <VirtualHost *:80> | |
| − | + | ServerName openkm.your-domain.com | |
| + | RedirectMatch ^/$ /OpenKM | ||
| + | <Location /OpenKM> | ||
| + | ProxyPass ajp://127.0.0.1:8009/OpenKM keepalive=On | ||
| + | ProxyPassReverse http://openkm.your-domain.com/OpenKM | ||
| + | </Location> | ||
| + | ErrorLog /var/log/apache2/openkm-error.log | ||
| + | CustomLog /var/log/apache2/openkm-access.log combined | ||
| + | </VirtualHost> | ||
| + | </source> | ||
| − | + | Finally restart Apache. | |
| − | + | == Windows == | |
| + | Install de apache webserver from http://httpd.apache.org/download.cgi ( windows binary no mod_ssl ) | ||
| − | + | Edit the C:\Archivos de programa\Apache Software Foundation\Apache2.2\conf\httpd.conf | |
| − | |||
| − | |||
| − | |||
<source lang="apache"> | <source lang="apache"> | ||
| − | + | # Enable proxy modules | |
| − | + | LoadModule proxy_module modules/mod_proxy.so | |
| − | + | LoadModule proxy_ajp_module modules/mod_proxy_ajp.so | |
| − | |||
| − | |||
| − | |||
| − | + | #Add in bottom | |
| − | + | NameVirtualHost *:80 | |
| − | + | <VirtualHost *:80> | |
| − | + | ServerName openkm.your-domain.com | |
| − | + | RedirectMatch ^/$ /OpenKM | |
| − | + | ||
| − | + | ProxyRequests Off | |
| − | + | ProxyVia On | |
| + | |||
| + | <Proxy *> | ||
| + | AddDefaultCharset off | ||
| + | Order deny,allow | ||
| + | Allow from all | ||
| + | Deny from All | ||
| + | </Proxy> | ||
| + | |||
| + | <Location /OpenKM> | ||
| + | ProxyPass ajp://127.0.0.1:8009/OpenKM | ||
| + | ProxyPassReverse http://openkm.your-domain.com/OpenKM | ||
| + | </Location> | ||
| + | |||
| + | ErrorLog logs/openkm-error_log | ||
| + | CustomLog logs/openkm-access_log common | ||
</VirtualHost> | </VirtualHost> | ||
</source> | </source> | ||
| − | + | {{Warning|If you have installed IIS started you should change apache port (Listen from 80 to other in httpd.conf)}} | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
== More info == | == More info == | ||
| Line 190: | Line 218: | ||
* [http://www.workingwith.me.uk/articles/scripting/mod_rewrite mod_rewrite, a beginner’s guide] | * [http://www.workingwith.me.uk/articles/scripting/mod_rewrite mod_rewrite, a beginner’s guide] | ||
* [http://www.thebuzzmedia.com/using-apache-virtual-hosts-and-proxypass-together/ Using Apache Virtual Hosts and ProxyPass Together] | * [http://www.thebuzzmedia.com/using-apache-virtual-hosts-and-proxypass-together/ Using Apache Virtual Hosts and ProxyPass Together] | ||
| − | |||
[[Category: Installation Guide]] | [[Category: Installation Guide]] | ||
| − | |||
Latest revision as of 07:05, 12 February 2015
Expose OpenKM directly from Tomcat or JBoss can be dangerous if you need the application to be accessed from Internet (for example https://issues.jboss.org/browse/JBAS-3861). As result you can be infected by PerlBot. Also this 8080 may be closed by a firewall. For these reasons, is a good idea expose your OpenKM installation through the standard web port 80. In the following steps we explain how to configure Apache to handle these request and forward to Tomcat application server using the AJP13 protocol.
From the Apache documentation: The AJP13 protocol is packet-oriented. A binary format was presumably chosen over the more readable plain text for reasons of performance. The web server communicates with the servlet container over TCP connections. To cut down on the expensive process of socket creation, the web server will attempt to maintain persistent TCP connections to the servlet container, and to reuse a connection for multiple request/response cycles.
| You can see how to configure Apache with SSL at Apache SSL and more article. |
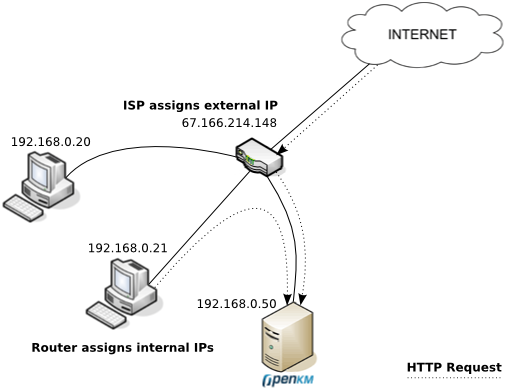
Internal IP vs external IP
Your OpenKM can be accessed from two different zones: Internet and LAN. This means that to access this server you need to use two IPs: external IP (Internet) and internal IP (LAN).
The internal IP address (also known as "local IP address") is the address that is assigned by your local network router that often begins with 192.168.x.x. These IP addresses can only be seen by other computers in your local network (LAN) and not by any computers connected in an external network such the Internet.
To reach the Internet or a computer in another network your computer is often assigned an external IP address, which can then be used to refer to the computer in your local network.
In the above picture, there are three computers in the local network that have each been assigned their own internal IP address by the router. The ISP is connected to the router and gives the router an external IP address that allows it to communicate with the Internet. On the Internet everyone sees your external IP address, but any information coming from the router is "converted" from the external IP address to the internal IP address.
So if you want your OpenKM installation accessible from both LAN and Internet, the trick here is configure the client computers to resolve your internal IP (192.168.0.50) if they are inside the LAN or the external IP if they are on Internet. To resolve the Internet IP (67.166.214.148) your computer uses the public DNS. So, you need to configure a sort of DNS server inside the LAN or modify every client host file to resolve to the internal IP.
Debian / Ubuntu
The first thing in to install the required Apache software. From Debian / Ubuntu you can install Apache with a single command:
$ sudo aptitude install apache2
Edit the file called /etc/apache2/apache2.conf and configure a ServerName to prevent warnings in the Apache startup process:
ServerRoot "/etc/apache2"
ServerName "your-domain.com"
Enable the proxy module, needed to forward petitions to JBoss:
$ sudo a2enmod proxy_ajp
Now create the configuration file /etc/apache2/sites-available/openkm.conf with this content:
<VirtualHost *>
ServerName openkm.your-domain.com
RedirectMatch ^/$ /OpenKM
<Location /OpenKM>
#ProxyRequests Off
#ProxyPreserveHost On
ProxyPass ajp://127.0.0.1:8009/OpenKM keepalive=On
ProxyPassReverse http://openkm.your-domain.com/OpenKM
</Location>
ErrorLog /var/log/apache2/openkm-error.log
CustomLog /var/log/apache2/openkm-access.log combined
</VirtualHost>
| See all ProxyPass parameter at Apache Module mod_proxy documentation. |
The VirtualHost ServerName must be other than ServerName in the main Apache configuration. Enable this site configuration:
$ sudo a2ensite openkm.conf
If after restart Apache you see a warning like:
[warn] NameVirtualHost *:80 has no VirtualHostsyou have to change the virtual host definition from <VirtualHost *> to <VirtualHost *:80> |
You have to enable explicitly the proxy access editing the Apache configuration file /etc/apache2/mods-available/proxy.conf:
<IfModule mod_proxy.c>
#turning ProxyRequests on and allowing proxying from all may allow
#spammers to use your proxy to send email.
ProxyRequests Off
<Proxy *>
AddDefaultCharset off
Order deny,allow
Allow from all
Deny from all
#Allow from .example.com
</Proxy>
# Enable/disable the handling of HTTP/1.1 "Via:" headers.
# ("Full" adds the server version; "Block" removes all outgoing Via: headers)
# Set to one of: Off | On | Full | Block
ProxyVia On
</IfModule>
Finally restart Apache:
$ sudo /etc/init.d/apache2 restart
Now you can access your OpenKM installation from http://openkm.your-domain.com/. Another advantage of using Apache is that you can log OpenKM access and generate web statistics.
The syntax is as follows to run syntax tests for configuration files only:
/usr/sbin/apache2 -t
Red Hat / CentOS
Here you can use the yum application manager to install Apache:
$ sudo yum install httpd
Remember to enable it at boot:
$ sudo chkconfig httpd --level 2345 on
Now create the file /etc/httpd/conf.d/openkm.conf with this content:
<VirtualHost *:80>
ServerName openkm.your-domain.com
RedirectMatch ^/$ /OpenKM
<Location /OpenKM>
ProxyPass ajp://127.0.0.1:8009/OpenKM keepalive=On
ProxyPassReverse http://openkm.your-domain.com/OpenKM
</Location>
ErrorLog /var/log/httpd/openkm-error.log
CustomLog /var/log/httpd/openkm-access.log combined
</VirtualHost>
After that, restart Apache to make effective this configuration.
$ sudo /etc/init.d/httpd restart
Mac OS X
Edit the file called /etc/apache2/apache2.conf and configure a ServerName, enable proxy modules and mod_proxy:
ServerRoot "/usr"
ServerName "your-domain.com"
LoadModule proxy_module libexec/apache2/mod_proxy.so
LoadModule proxy_ajp_module libexec/apache2/mod_proxy_ajp.so
<IfModule mod_proxy.c>
ProxyRequests Off
<Proxy "*">
AddDefaultCharset off
Allow from all
Deny from all
Order Deny,Allow
</Proxy>
ProxyVia On
</IfModule>
Now create the configuration file /etc/apache2/sites/openkm.conf with this content:
<VirtualHost *:80>
ServerName openkm.your-domain.com
RedirectMatch ^/$ /OpenKM
<Location /OpenKM>
ProxyPass ajp://127.0.0.1:8009/OpenKM keepalive=On
ProxyPassReverse http://openkm.your-domain.com/OpenKM
</Location>
ErrorLog /var/log/apache2/openkm-error.log
CustomLog /var/log/apache2/openkm-access.log combined
</VirtualHost>
Finally restart Apache.
Windows
Install de apache webserver from http://httpd.apache.org/download.cgi ( windows binary no mod_ssl )
Edit the C:\Archivos de programa\Apache Software Foundation\Apache2.2\conf\httpd.conf
# Enable proxy modules
LoadModule proxy_module modules/mod_proxy.so
LoadModule proxy_ajp_module modules/mod_proxy_ajp.so
#Add in bottom
NameVirtualHost *:80
<VirtualHost *:80>
ServerName openkm.your-domain.com
RedirectMatch ^/$ /OpenKM
ProxyRequests Off
ProxyVia On
<Proxy *>
AddDefaultCharset off
Order deny,allow
Allow from all
Deny from All
</Proxy>
<Location /OpenKM>
ProxyPass ajp://127.0.0.1:8009/OpenKM
ProxyPassReverse http://openkm.your-domain.com/OpenKM
</Location>
ErrorLog logs/openkm-error_log
CustomLog logs/openkm-access_log common
</VirtualHost>
| If you have installed IIS started you should change apache port (Listen from 80 to other in httpd.conf) |
More info
For more info, visit: